Java Runtime Environment (JRE) – How to Import Certificates
A lot of company applications are actually using the Java Runtime Environment (JRE) and a lot of them are integrated in the Internet Explorer using local adresses. When you open these kind of applications you will receive an error message that the application can not be trusted eventhough you provided your own root certificates by group policies. One big problem of the JRE is that it completelly ignores the Windows certificate stores. Instead of using the windows certificate store it uses its own implementation.
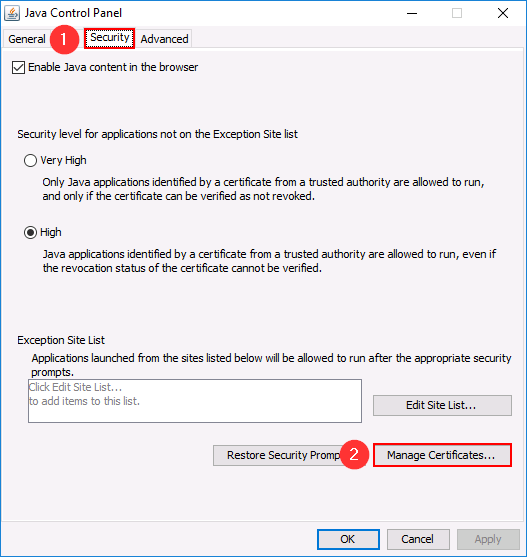
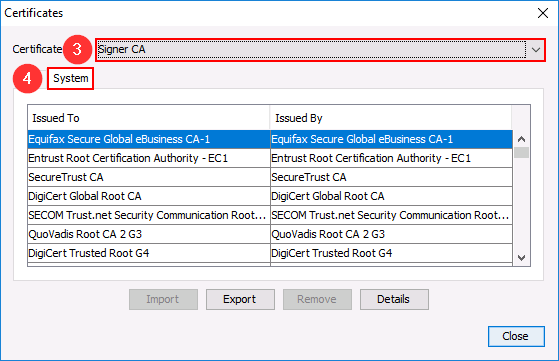
Java certificates are stored in a file called cacerts located at C:\Program Files (x86)\Java\jre1.x.x_xxx\lib\security\ You can open javacpl.exe to get a graphical overview about the content:
You can import certificates as user certificates by the graphical user interface but you are not allowed to add any system certificates. This is only possible by using keytool.exe that is located in every standard JRE installation C:\Program Files (x86)\Java\jre1.8.0_144\bin\keytool.exe
The following command will import the certificate “C:\certificate.cer” to the keystore “cacerts” that is protected by the password “changeit”. If you have installed the JRE with default settings the standard keystore is always called “cacerts” and always protected by the password “changeit”.
keytool.exe -import -storepass "changeit" -keystore "C:\Program Files (x86)\Java\jre1.8.0_144\lib\security\cacerts" -alias certificate.cer -file "C:\certificate.cer" -noprompt
To get this command running without any user interaction I suggest to run it as a PowerShell script in system context during client login. This is the only way to ensure that private root certitificates are always up to date.
Official keytool documentation: https://docs.oracle.com/javase/6/docs/technotes/tools/windows/keytool.html
Solution:
If we are talking about enterprise a solution is to call a script checking a certificate folder on a network share everytime a computer gets restarted. I’ve used the following script a lot of times with the help of group policies. Feel free to use it in your own environment.
This script needs the following variables to be declared:
- $JavaCertificateFolder – Defines a share that is hosting all root certificates ending by .cer . The script will automatically import all certificates stored in the share.
- $JRE_HOME – Defines the Java home path. With that information the script can locate the keytool.exe and your cacerts store.
- $log – Defines a logging path. The script will always write a log to the path and name you’ve entered.
################## Edit this area #####################
$JavaCertificateFolder = "\\customer.local\share\Java\"
$JRE_HOME = "C:\Program Files (x86)\Java\jre1.8.0_144\"
$log = "$env:LOCALAPPDATA\Temp\W10_JavaKeystoreImport.log"
#######################################################
Start-Transcript -path $log
Write-Output "---------------------------------------"
Write-Output "Check JRE_HOME"
Write-Output "---------------------------------------"
Write-Output ""
if(Test-Path $JRE_HOME){
Write-Output "[X] OK"
Write-Output ""
Write-Output "---------------------------------------"
Write-Output "Check for $JavaCertificateFolder"
Write-Output "---------------------------------------"
Write-Output ""
try{
$certificates=Get-ChildItem -Path $JavaCertificateFolder -Filter *.cer -ErrorAction Stop
}
catch{
Write-Output "ERROR: Could find *.cer in $JavaCertificateFolder"
Write-Output "ERROR: execution aborted"
Stop-Transcript
break;
}
Write-Output "[X] OK"
Write-Output ""
$JavaKeyTool = $JRE_HOME + "bin\keytool.exe"
$JavaCertStore = $JRE_HOME + "lib\security\cacerts"
Write-Output "---------------------------------------"
Write-Output "Check for JavaKeyTool & JavaCertStore"
Write-Output "---------------------------------------"
Write-Output ""
if(Test-Path $JavaKeyTool){
if(Test-Path $JavaCertStore){
Write-Output "[X] OK"
Write-Output ""
Write-Output "---------------------------------------"
Write-Output "Variables"
Write-Output "---------------------------------------"
Write-Output ""
Write-Output "Certificate Folder: $JavaCertificateFolder"
Write-Output "Certificate Store: $JavaCertStore"
Write-Output "Keytool Location: $JavaKeyTool"
Write-Output ""
Write-Output "---------------------------------------"
Write-Output "Certificate Import"
Write-Output "---------------------------------------"
Write-Output ""
#Certificate Import
foreach ($certificate in Get-ChildItem -Path $JavaCertificateFolder -Filter *.cer) {
$certfullpath = $JavaCertificateFolder + $certificate
Write-Output "Import Certificate: $certfullpath"
#Import into Keystore
$AllArgs = @('-import', '-storepass ', 'changeit', '-keystore ',
$JavaCertStore, '-alias ', $certificate, '-file ', $certfullpath, '-noprompt')
& $JavaKeyTool $AllArgs
Write-Output ""
}
}
else{
Write-Output "[X] ERROR"
Write-Output "ERROR: $JavaCertStore not available"
Write-Output "ERROR: execution aborted"
Stop-Transcript
break;
}
}
else{
Write-Output "[X] ERROR"
Write-Output "ERROR: $JavaKeyTool not available"
Write-Output "ERROR: execution aborted"
Stop-Transcript
break;
}
}
else {
Write-Output "[X] ERROR"
Write-Output "ERROR: $JRE_HOME not available"
Write-Output "ERROR: execution aborted"
Stop-Transcript
break;
}
Stop-Transcript
How does the script work?
- First the script validates if your declared variables $JavaCertificateFolder , $JRE_HOME and $log are valid.
- In the next step the script will check if $JavaCertificateFolder does contain any certificate files ending with .cer .
- The script will automatically set path to the keytool.exe and to the cacerts store.
- In the last step the script will execute the keytool.exe with the above eplained command for certificate import.
- All actions done by the script will be logged to the location you specified in $log. By default the path is C:\Users\username\AppData\Local\Temp\W10_JavaKeystoreImport.log
How can I validate that everything worked as expected?
- Check the log file you’ve defined in $log. If you can’t find any messages containing [X] ERROR everything regarding your variables is fine.
- Check javacpl.exe to ensure that your certificates got imported.
- Take a deep look in your log file starting at Certificate Import. The automatic import will start at this point!
Transcript started, output file is C:\Users\<removed>\AppData\Local\Temp\W10_JavaKeystoreImport.log --------------------------------------- Check JRE_HOME --------------------------------------- [X] OK --------------------------------------- Check for C:\Users\<removed>\Desktop\Neuer Ordner\ --------------------------------------- [X] OK --------------------------------------- Check for JavaKeyTool & JavaCertStore --------------------------------------- [X] OK --------------------------------------- Variables --------------------------------------- Certificate Folder: C:\Users\<removed>\Desktop\Neuer Ordner\ Certificate Store: C:\Program Files (x86)\Java\jre1.8.0_144\lib\security\cacerts Keytool Location: C:\Program Files (x86)\Java\jre1.8.0_144\bin\keytool.exe --------------------------------------- Certificate Import --------------------------------------- Import Certificate: C:\Users\<removed>\Desktop\Neuer Ordner\Certificate1.cer keytool.exe : Certificate was added to keystore Import Certificate: C:\Users\<removed>\Desktop\Neuer Ordner\Certificate2.cer keytool.exe : Certificate was added to keystore Transcript stopped, output file is C:\Users\<removed>\AppData\Local\Temp\W10_JavaKeystoreImport.log
Transcript started, output file is C:\Users\<removed>\AppData\Local\Temp\W10_JavaKeystoreImport.log --------------------------------------- Check JRE_HOME --------------------------------------- [X] OK --------------------------------------- Check for C:\Users\<removed>\Desktop\Neuer Ordner\ --------------------------------------- [X] OK --------------------------------------- Check for JavaKeyTool & JavaCertStore --------------------------------------- [X] OK --------------------------------------- Variables --------------------------------------- Certificate Folder: C:\Users\<removed>\Desktop\Neuer Ordner\ Certificate Store: C:\Program Files (x86)\Java\jre1.8.0_144\lib\security\cacerts Keytool Location: C:\Program Files (x86)\Java\jre1.8.0_144\bin\keytool.exe --------------------------------------- Certificate Import --------------------------------------- Import Certificate: C:\Users\<removed>\Desktop\Neuer Ordner\Certificate1.cer keytool error: java.lang.Exception: Certificate not imported, alias <Certificate1.cer> already exists Import Certificate: C:\Users\<removed>\Desktop\Neuer Ordner\Certificate2.cer keytool error: java.lang.Exception: Certificate not imported, alias <Certificate2.cer> already exists Transcript stopped, output file is C:\Users\<removed>\AppData\Local\Temp\W10_JavaKeystoreImport.log
Transcript started, output file is C:\Users\<removed>\AppData\Local\Temp\W10_JavaKeystoreImport.log --------------------------------------- Check JRE_HOME --------------------------------------- [X] OK --------------------------------------- Check for C:\Users\<removed>\Desktop\Neuer Ordner\ --------------------------------------- [X] OK --------------------------------------- Check for JavaKeyTool & JavaCertStore --------------------------------------- [X] ERROR ERROR: C:\Program Files (x86)\Java\jre1.8.0_144\bin\keytool.exe not available ERROR: execution aborted Transcript stopped, output file is C:\Users\<removed>\AppData\Local\Temp\W10_JavaKeystoreImport.log